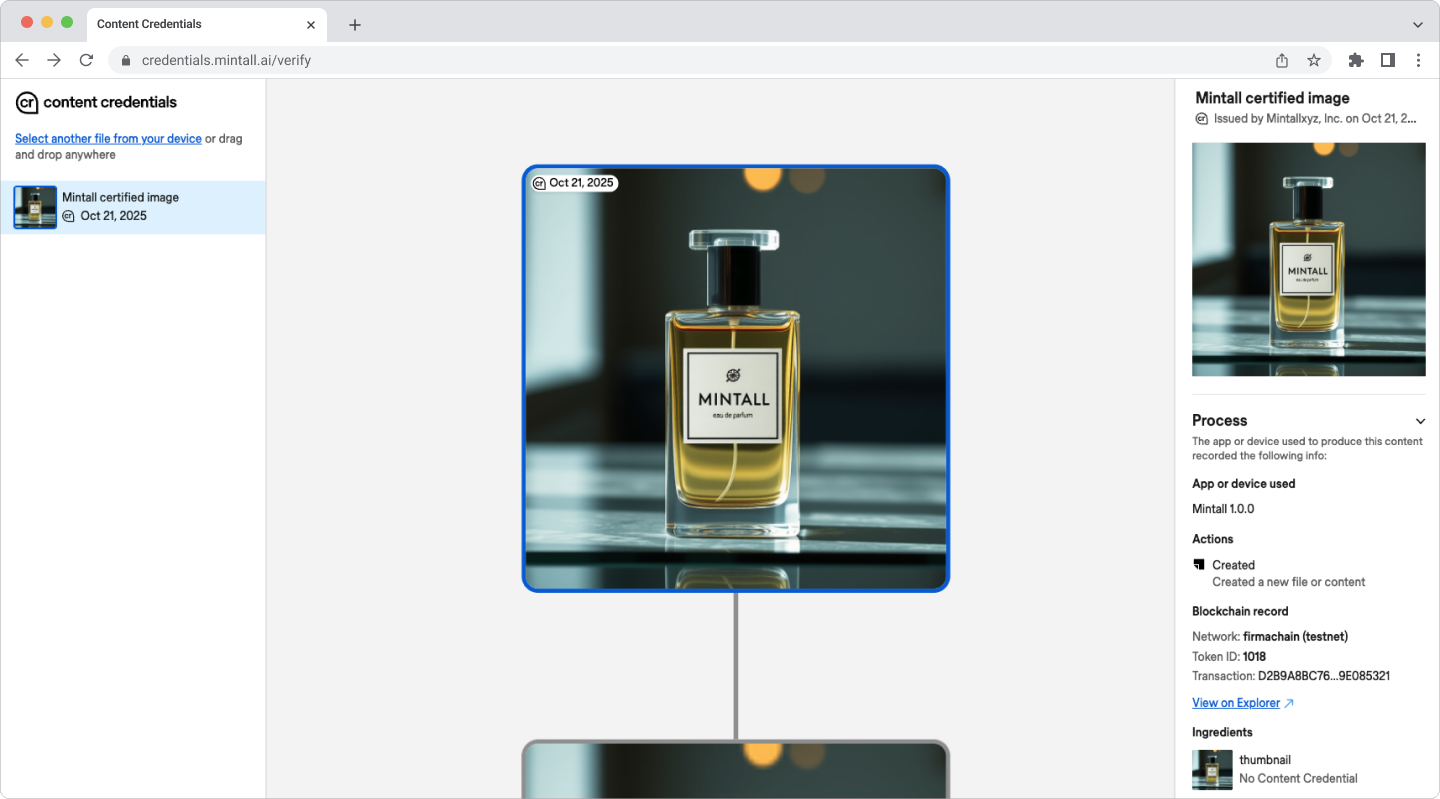
If anchoring references are present, anyone can independently verify timestamps via a public explorer.
Verify embedded C2PA metadata with tamper-evident signatures and extract normalized claims for downstream checks.
Verification artifacts remain checkable by third parties and automation, without relying on private state.